Application Security
Computer Security
Project details
Description
Gained root access across a series of 8 progressively hardened C binaries by reverse engineering and crafting low-level exploits in Python:
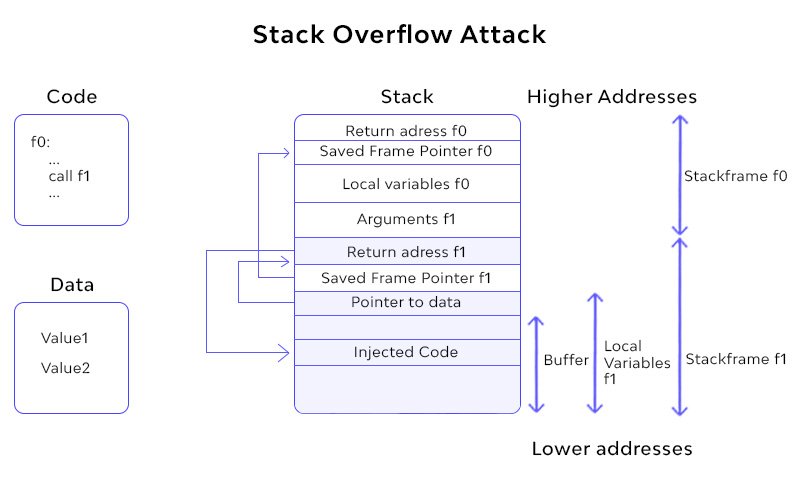
- Overwrote return addresses using buffer overflow to redirect control flow, launching shellcode and executing privileged instructions
- Exploited limited-copy and numeric buffer overflows to bypass stack protections and execute injected shellcode
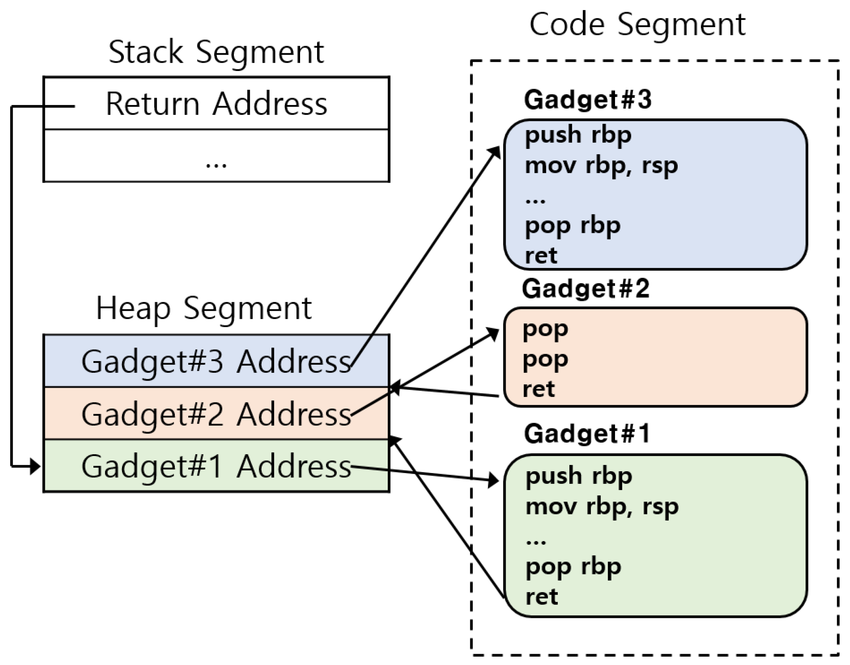
- Bypassed DEP and ASLR using return-to-libc and randomized padding techniques
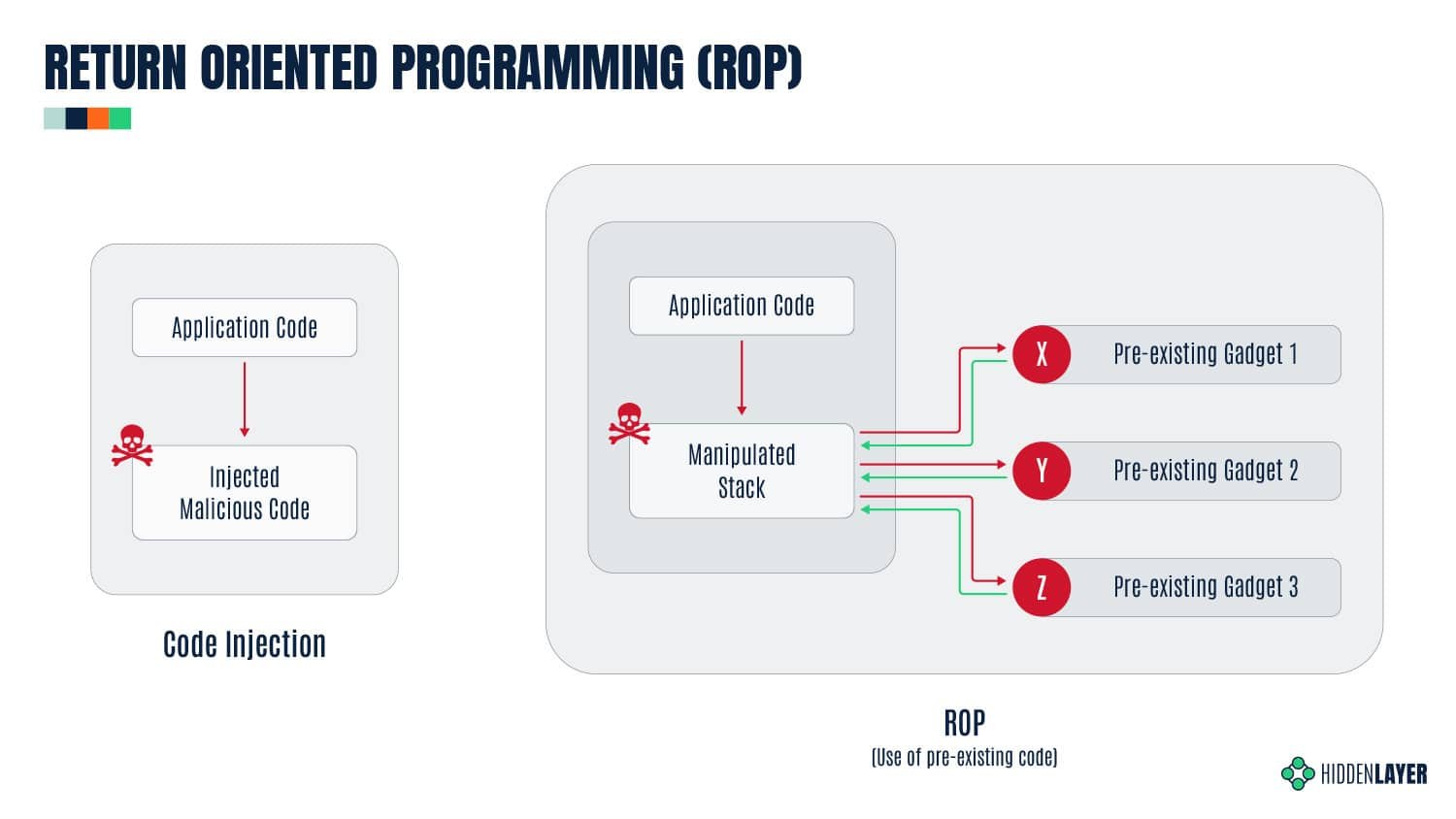
- Executed Return-Oriented Programming by constructing a complete ROP chain using gadgets identified via ROPgadget to invoke setuid(0) and execve("/bin/sh"), successfully bypassing DEP to gain root access
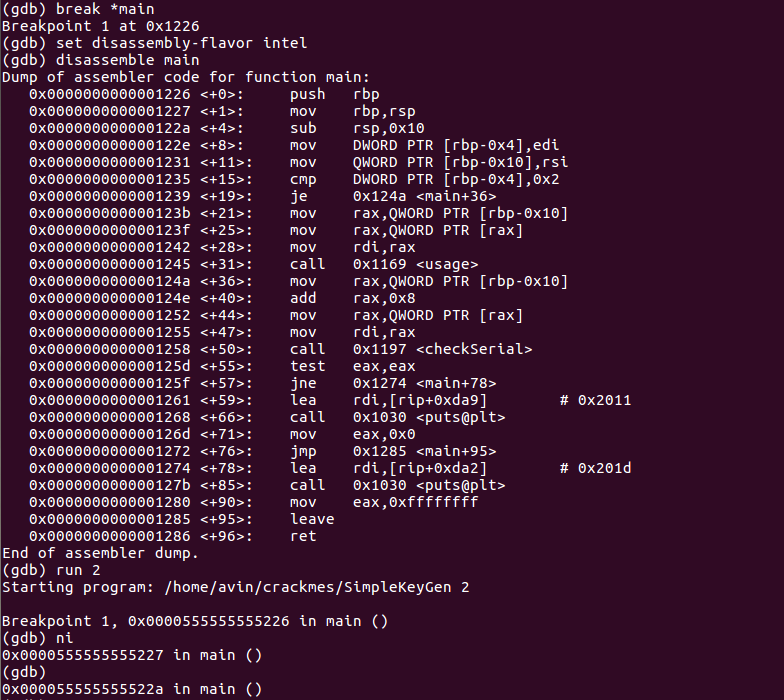
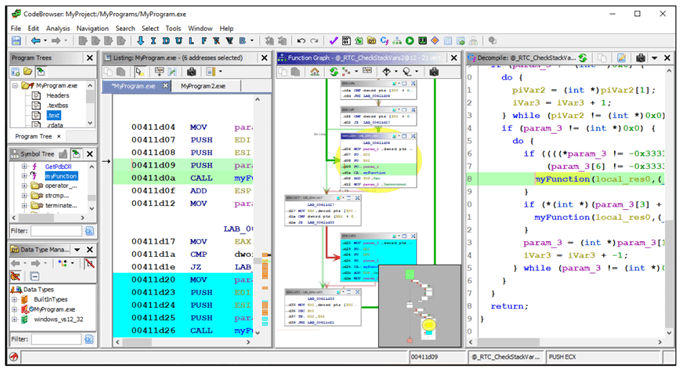
- Reverse engineered a closed-source binary with Ghidra, analyzed control flow and logic, and exploited a hidden buffer overflow to trigger privileged behavior
-
Start Date:
Mar 12th, 2025 -
End Date:
Apr 2th, 2025 -
Github:
Private -
Course:
EECS388 -
Course Topic:
Computer Security
7+
Years of Coding Experience
25
Completed CS Projects
3+